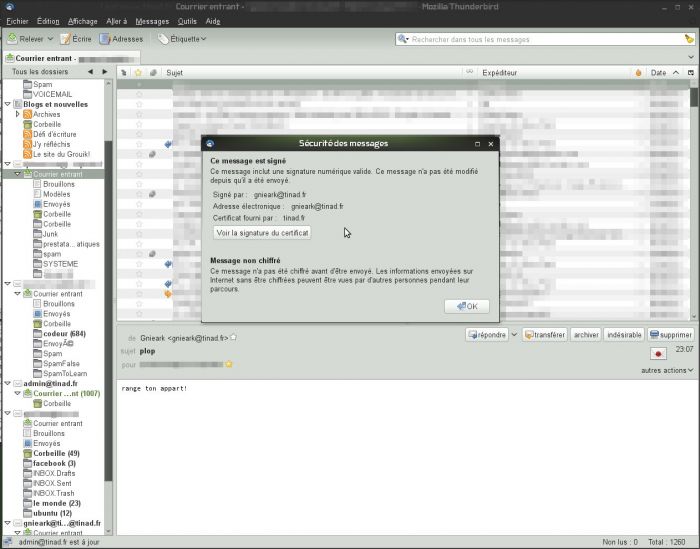
Signer ses mails
 Nos avons vu dans ce billet comment faire une autorité de certification. Voyons comment s'en servir pour créer des certificats PKCS12 servant à signer les mails.
Ça n'a aucun intérêt car seuls les personnes ayant votre certificat racine pourront vérifier la signature (enfin pas eux, leur logiciel client mail). C'est juste pour le fun ce billet, Pour des certificats de signature de mail, il vaut mieux regarder du coté des autorités de certification telles que thawte verisign etc....
Nos avons vu dans ce billet comment faire une autorité de certification. Voyons comment s'en servir pour créer des certificats PKCS12 servant à signer les mails.
Ça n'a aucun intérêt car seuls les personnes ayant votre certificat racine pourront vérifier la signature (enfin pas eux, leur logiciel client mail). C'est juste pour le fun ce billet, Pour des certificats de signature de mail, il vaut mieux regarder du coté des autorités de certification telles que thawte verisign etc....
Creer le certificat et sa clé:
cd ~/CERT openssl req -new -keyout gnieark\@tinad.fr-key.pem -out gnieark\@tinad.fr-req.pem -days 365
Adaptez les réponses à vos besoins, Cependant le "Organization Name" doit etre le même que le certificat racine:
Generating a 1024 bit RSA private key ...++++++ ...++++++ writing new private key to 'gnieark@tinad.fr-key.pem' Enter PEM pass phrase: Verifying - Enter PEM pass phrase: ----- You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [AU]:FR State or Province Name (full name) [Some-State]:France Locality Name (eg, city) []:Rouen Organization Name (eg, company) [Internet Widgits Pty Ltd]:tinad Organizational Unit Name (eg, section) []:tinad.fr Common Name (eg, YOUR name) []:gnieark@tinad.fr Email Address []:gnieark@tinad.fr Please enter the following 'extra' attributes to be sent with your certificate request A challenge password []: An optional company name []:
Signer le certificat:
cd ~ openssl ca -out CERT/gnieark\@tinad.fr-cert.pem -infiles CERT/gnieark\@tinad.fr-req.pem
Using configuration from /usr/lib/ssl/openssl.cnf
Enter pass phrase for ./demoCA/private/cakey.pem:
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number:
81:c4:e6:a3:37:dc:50:0a
Validity
Not Before: Jun 25 09:11:12 2010 GMT
Not After : Jun 22 09:11:12 2020 GMT
Subject:
countryName = FR
stateOrProvinceName = France
organizationName = tinad
organizationalUnitName = tinad.fr
commonName = gnieark@tinad.fr
emailAddress = gnieark@tinad.fr
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
1F:AD:68:6F:CE:E3:33:23:6C:2E:4D:86:FD:FC:CD:A4:D9:F5:8F:32
X509v3 Authority Key Identifier:
keyid:2A:96:75:31:A5:A1:0F:1C:19:5E:8D:64:6F:DD:30:44:27:28:23:15
Netscape CA Revocation Url:
http://www.tinad.fr/certs/ca-crl.pem
Netscape CA Policy Url:
http://www.tinad.fr/certs/policys.pdf
Certificate is to be certified until Jun 22 09:11:12 2020 GMT (365 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
Convertir le certificat au format PKCS:
openssl pkcs12 -in CERT/gnieark\@tinad.fr-cert.pem -inkey CERT/gnieark\@tinad.fr-key.pem -certfile demoCA/cacert.pem -out CERT/gnieark\@tinad.fr.p12 -name "grouik" -export
Enter pass phrase for CERT/gnieark@tinad.fr-key.pem: Enter Export Password: Verifying - Enter Export Password:
Maintenant il faut chopper gnieark@tinad.fr.p12 et le mettre sur son ordinateur.
Le paramétrage de Thunderbird est simple:
Editions paramètres des comptes, dans la partie "sécurité", Il y a tout ce qu'il faut. Ça permet d'envoyer des messages signée: la classe.